More Netbus 2.0 Server And Client videos. VNAP.NetBuster Proxy Pro is a GNU Licenced Freeware Proxy Server and Client. NetBus 2.0 Pro was released in. SMTP communication between mail servers. Remote Desktop Services - Wikipedia. Remote Desktop Services (RDS), known as Terminal Services in Windows Server 2. NetBus consists of a client and a server program. The server program is called 'NetBus Server' or 'NBSvr.exe'. It simulates the NetBus server, you see who's connecting and you can send THEM messages and play tricks on them. Carl-Fredrik Neikter released NetBus 2.0 Pro in February 1999. Neikter: The NetBus 1.x versions were supposed to. It even deletes the data logged by the server! This also works if you have already installed a 'NetBus 2.0 Server' To remove or reconfigure you best use the 'NetBus 2.0 Client'. FAQs And Hints to NetBus 2.0 Pro: Please read this document prior to writing an e-mail to me or asking me questions via ICQ. Links to Netbus/ NetBus 2.0 Pro.
- Netbus 2 0 Server And Client Software Update
- Netbus 2 0 Server And Client Software
- Netbus 2 0 Server And Client Software List
- Netbus 2 0 Server And Client Software Download
- Net2 is an advanced PC based access control solution. Our Net2 software offers centralised administration and control of sites with up to 1,000 doors and 50,000 users. Perfectly tailor access privileges to groups or individuals quickly and easily using our intuitive, user-friendly software. Event reports can be generated in a few clicks and the.
- Using Net2 Client software The Net2 Client software allows Net2 operators to. Remotely connect with the PC running the Net2 application and server software. Multiple versions of this application can be used at the same time and can be established over most TCP/IP and VPN networks. Client software presents the operator with a list of.

Slovenianversion
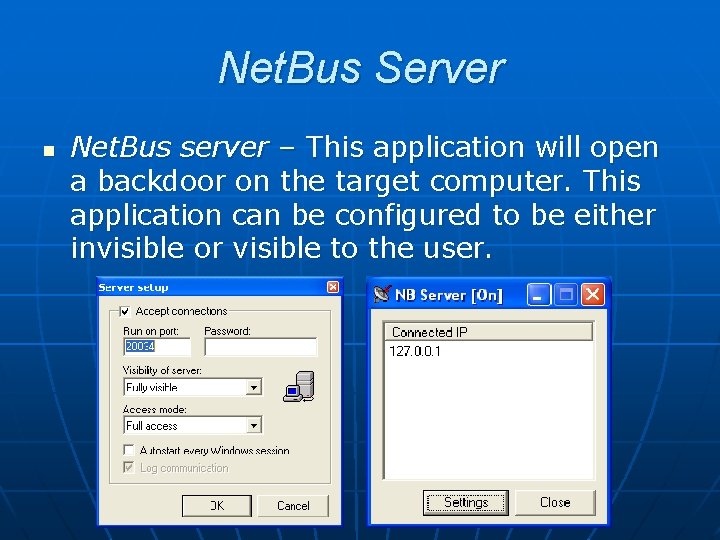
WHAT IS NETBUS?
Netbus is a so-called trojan horse,similar to Back Orifice, but slightly different - it works not only underWindows 95/98, but also Windows NT. If Netbus server has been installedon your computer, someone can take control over it using Netbus clienton theirs.
HOW DOESIT WORK?
Netbus consists of two parts: a server(which has to be installed on the victim's computer), and a client (installedon the intruder's computer). The two communicate using TCP/IP protocols.
Netbus also has the option to finda computer with an active Netbus server at random.
This is how the client looks like:
HOW CAN MY COMPUTER GET INFECTEDWITH NETBUS?
Netbus is usually spread with a filenamed PATCH.EXE, but be aware that this file can be renamed. (e.g. CATCH.EXE)Once the file has been run, it makes an entry in Windows registry at:
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
How can this happen? For example:you are chatting with someone. They send you an .exe file, and trick intorunning it. As soon as you do that, Netbus server is installed on yourcomputer, the intruder connects his client with your server - and VOILA,he has access to everything on your computer!
You can get the file also by downloadingit from the internet, via e-mail, or any other means.
WHAT CAN SOMEONE DO TO YOURCOMPUTER USING NETBUS?
1. Open/close the CD-ROM tray onceor in intervals (specified in seconds);
2. Show optional BMP or JPG image(full path allowed);
3. Swap mouse buttons - the rightbutton gets the left button's functions and vice versa;
4. Start optional application (fullpath allowed);
5. Play optional WAV sound-file(full path allowed);
6. Point the mouse to optional coordinates;
7. Show a message dialog on thescreen and allow the user on remote system to answer it;
8. Shutdown Windows, reboot, logoffor power off;
9. Go to an optional URL withinthe default web-browser;
10. Send keystrokes to the activeapplication on the target computer;
11. Listen for keystrokes on remotesystem and save them to file;
12. Get a screenshot from remotecomputer;
13. Return information about thetarget computer;
14. Upload any file to the targetcomputer or update the server part of NetBus;
15. Increase and decrease the sound-volume;
16. Record sounds that the microphonecatch - to listen what happens in the room where remote computer is;
17. Make click sounds every timea key is pressed;
18. Download and deletion of anyfile from the target system;
19. Blocking certain keys on theremote system keyboard;
20. Password-protection managementof the remote server;
21. Show, kill and focus windowson remote system.
I THINK MY COMPUTER HAS BEENINFECTED WITH NETBUS. HOW DO I MAKE SURE OF THAT?
1. You have to check your registry.(here are the instructions)If you do find it there, you can also delete it, as instructed. (WARNING!Users not used to working with registry should consult an expert! Deletingthe wrong file could cause Windows to not work properly)
2. Delete the file that infectedyour computer.
COMPUTERINTRUSION IS ILLEGAL IN MOST COUNTRIES ! You should check the laws in yourcountry. If your computer has been broken into, report this to the authorities!Remember, in that case, DO NOT delete anything. If you delete the files,you are destroying the evidence, and therefor making it impossible to tracethe intruder!
MORE INFO ON NETBUS:
________________________________________________________________________________________________
Privacy Software Corporation SecurityAdvisory
Tuesday, September 1, 1998
NETBUS INTERNET TROJAN HORSE PROGRAM
SYNOPSIS:
A Swedish programmer has releaseda Windows 95/98 trojan horse program named 'Netbus.' Netbus consists ofa client program called Netbus which is run on a remote computer to gainaccess to any computer connected to a TCP/IP network or the internet. Anexecutable server program is required to be installed on the victim's computerto permit the remote site access to the victim's computer in a manner similarto Cult of the Dead Cow's 'Back Orifice' program. As is the case with 'BackOrifice,' this program exploits security vulnerabilities in the Windows95 and Windows 98 platform and does not function on Windows NTsystems at the time of this advisory. 'Netbus does infectand affect NT systems. Our own internal research has proven this, and wehave received many reports of Netbus intrusion into customer's NT systems.'(written in mail from Privacy Software Corporation CEO as of November 10,1998) Reported delivery modes include transfer through IRC andAOL chat rooms, email file attachments, exploits of security holes in browsersand email programs and physical installation on machines.

The server program for the Netbustrojan horse can be given any name by the party who places it on the victim'smachine which makes it difficult, but not impossible to identify afterit has been installed. The server is provided under the name of PATCH.EXEbut exploiters of this trojan horse program are reminded that they shouldchange the name of the server program or package it within another innocuousprogram for delivery and installation on the victim's machine.
Privacy Software Corporation's 'BOCleanversion 2.01' software, designed to detect and defeat the 'Back Orifice'trojan horse program, is fully effective in removing the Netbus serverregardless of the filename or manner of delivery and, as is the case with'Back Orifice,' can also disable this program instantly upon detection.BOClean version 2.01 will also remove the files and registry hooks withoutthe need to disconnect from the internet or reboot the victim's machine.This precludes the risks of registry editing and possible loss of dataand permits the victim to remove the program and continue their use ofa TCP/IP connection without loss of work or time.
The server program can also be removedmanually if it is delivered in its native state with the default filenameof 'PATCH.EXE.' Since the server program can be given any name, the registrywill have to be examined to determine the name of the server program. Aknowledge of legitimate registry entries in the particular machine is requiredin order to determine the key which contains the pointer to the Netbusserver program. Once the added file is determined, the registry entry canbe removed and the machine rebooted to permit deletion of the server file.A KeyHook.DLL file is also placed in the WINDOWS or WINDOWSSYSTEM directorywhich replaces any copies of this file which may have been installed withother shareware legitimately. It will be necessary to replace the KeyHook.DLLfile with a copy from the original install disks after removal.
While the server is a completelydifferent design from 'Back Orifice,' its behaviors are similar as is themeans of exploitation of the victim's machine. The server is similar tobut not the same as the server used in the 'Master's Paradise' exploit.
CAPABILITIES:
The Netbus server permits anyoneusing the Netbus client to remotely control the victim's machine. The capabilitiesof the Netbus program are not as significant as 'Back Orifice' but PrivacySoftware Corporation has already received reports of this and similar trojanhorse programs from BOClean customers in actual operation on their machines.We quote from the documentation shipped with the Netbus program below verbatim:
Open/close the CD-ROM once or inintervals (specified in seconds).
Show optional image. If no fullpath of the image is given it will look for it in the Patch-directory.The supported image-formats is BMP and JPG.
Swap mouse buttons the right mousebutton gets the left mouse button's functions and vice versa.
Start optional application.
Play optional sound-file. If nofull path of the sound-file is given it will look for it in the Patch-directory.The supported sound-format is WAV.
Point the mouse to optional coordinates.You can even navigate the mouse on the target computer with your own!
Show a message dialog on the screen.The answer is always sent back to you!
Shutdown the system, logoff theuser etc.
Go to an optional URL within thedefault web-browser.
Send keystrokes to the active applicationon the target computer! The text in the field Message/text will be insertedin the application that has focus. (| represents enter).
Listen for keystrokes and send themback to you!
Get a screendump! (should not beused over slow connections)
Return information about the targetcomputer.
Upload any file from you to thetarget computer! With this feature it will be possible to remotely updatePatch with a new version.
Increase and decrease the sound-volume.
Record sounds that the microphonecatch. The sound is sent back to you!
Make click sounds every time a keyis pressed!
Download and deletion of any filefrom the target. You choose which file you wish to download/delete in anice view that represents the harddisks on the target!
Keys (letters) on the keyboard canbe disabled.
Password-protection management.
Show, kill and focus windows onthe system.
The ability to turn on a microphoneis particularly threatening as this could permit the perpetrator the abilityto listen to room audio and in effect 'bug' the victim's room without detection.The ability to monitor keystrokes is also of concern as is the abilityto read and write files or possibly destroy the operating system.
MANUAL REMOVAL OF NETBUS SERVER:
The Netbus server will install itsprogram in the registry under the HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunkey and may have a dos-like command switch such as /nomsg, /noadd or similarswitch. In some cases this clue will not appear. The registry entry willpoint to the name of the file as the subkey name and will have as its valuea pointer to the location where the server is installed.
It is necessary to remove the registrysubkey first. It will not be possible to remove the program file whilethe server is running and you may also be prevented from shutting downthe computer. A reboot will be required in order to restart the machinewithout the Netbus server being reloaded at which time the file pointedto in the registry can be removed without further risk.
As a result, care should be takento back up your registry first as well as your programs and files in theevent that removal of the registry entry results in damage to your system.Use of Privacy Software Corporation's 'BOClean version 2.01' program willsafeguard against this possibility by removing the program and its registryentries automatically without risk of damage.
COPYRIGHTED MATERIAL:
Copyright (c) 1998 by Privacy SoftwareCorporation.
Permission is granted for the retransmissionof this advisory by electronic means. It is not to be edited in any waywithout the express consent of Privacy Software Corporation. Requests toreprint this information in whole or in part should be directed to technology@privsoft.com.
Disclaimer: The information withinthis advisory may change without notice and is provided by Privacy SoftwareCorporation AS IS. No warrantees, express or implied, are provided withrespect to this information nor should any be construed by the transmissionof this information. Any use of this information or its recommendationsis solely at the risk of the user.
Contact Privacy Software Corporationat http://www.privsoft.com, http://www.nsclean.com, email to technology@privsoft.com.Copies of the Netbus distribution as captured by Privacy Software Corporationwill only be provided to recognized security interests and responsible,recognized members of the press with the technical capability to conductindependent research on this trojan horse program or in the alternative,we will provide the URL where the programs can be obtained independently.Copies will NOT be provided by us to any other parties. Privacy SoftwareCorporation reserves the right to refuse transmission without further explanation.Under the provisions of Privacy Software Corporation's customer and websiteprivacy policies, we cannot divulge email from our customers regardingtheir experiences with these trojan horse programs nor can we divulge theiridentities under any circumstances.
Free updates are available to existingBOClean customers of Privacy Software Corporation to include coverage ofthis new trojan horse exploit. Copies of BOClean version 2.01 now shippingalready contain these updates. BOClean customers should visit the BOCleansupport page at http://www.nsclean.com/supboc.html for further details.
***********************************************************************************************************
(copied from http://post.blackbox.at/fcweb/Computertalk_Hackers/BONetbus_Infos.htm)
_________________________________________________________________________________________________________________________________________________________
Links:
Moreinfo on NetBus
Thehomepage of Netbus' author
Netbus 2 0 Server And Client Software Update
Netbus 2 0 Server And Client Software
Netbus 2 0 Server And Client Software List
Webmaster’s Note: The following is an advisory issued by Internet SecuritySystems, Inc., a commercial company which makessecurity software. I took the liberty of deleting 2 URLs for downloading theattacks themselves, to minimize our role in facilitating new attacks. I alsoreplaced the 2 broken links providing fix information for NetBus with analternative, trustworthy source. For a more detailed, illustrated guide to theBack Orifice backdoor mentioned in this article, please also see our own guideat Back Orifice backdoor-Jolo
Copyright (C) 1996,1997 Joseph Lo and many
Netbus 2 0 Server And Client Software Download
others.